You get a phone call. It's your bank's fraud department. The voice sounds professional, calm, maybe a little urgent. They've detected suspicious activity on your account and need to verify some information to protect your money. So you do what any reasonable person would do—you help them out. Except it wasn't your bank. It was a scammer using a $0 AI tool that cloned a voice in about 3 seconds.
This is vishing—voice phishing—and it's exploding. According to the CrowdStrike 2025 Global Threat Report, vishing attacks increased by 442% in the second half of 2024 alone. And in Q1 2025? Deepfake-enabled vishing surged by 1,633%.
Those numbers aren't a typo. This isn't some distant problem affecting Fortune 500 companies. It's hitting regular people and small businesses right now. (If you missed the broader picture, I covered it in my 2025 scam recap.)
The $0 Voice Clone Problem
Here's the thing that makes this different from the obvious scam calls we've all been ignoring for years: the voice on the other end might actually sound like someone you know.
McAfee Labs spent two weeks testing AI voice cloning tools and found more than a dozen freely available on the internet. No hacking skills required. No expensive software. Just upload a few seconds of someone's voice—pulled from a YouTube video, a podcast, a conference recording, even a TikTok—and the AI does the rest.
Three seconds of audio is all it takes to create a convincing clone. That CEO who did a webinar last month? That's enough. The boss who left a voicemail? Plenty. Your grandma who posts birthday videos on Facebook? Jackpot.
Why This Works So Well
Our brains are wired to trust familiar voices. When you hear what sounds like your boss, your bank, or your mom, you don't stop to analyze the audio frequencies. You just... believe it.
And here's the uncomfortable part: 70% of people surveyed said they weren't confident they could tell the difference between a cloned voice and the real thing. That's not because people are dumb. It's because the technology is genuinely that good now.
One in four people have already experienced an AI voice cloning scam or know someone who has. And of those who received a cloned voice message? 77% lost money.
The $25 Million Phone Call
If you think this only catches people off guard for small amounts, think again.
In early 2025, a multinational firm lost nearly $25 million after an employee received a voicemail that sounded exactly like their CEO. The message authorized an urgent fund transfer. The voice was perfect—same tone, same cadence, same verbal tics. The employee followed instructions. The money was gone within hours.
That's the ceiling. The floor is more common: someone loses $500 to $3,000 to a cloned voice pretending to be a grandchild in trouble, a boss needing gift cards, or a bank's fraud department needing to "verify" your account.
How the Scam Actually Works
The playbook usually looks like this:
- They find a voice sample. LinkedIn videos, company webinars, podcasts, social media. Any public audio works.
- They clone it. Free AI tools turn that sample into a voice they can control. They type words; the clone speaks them.
- They add context. They research you. They know where you bank, who your boss is, maybe even what project you're working on. Social media makes this embarrassingly easy.
- They create urgency. "There's been unauthorized activity." "This is time-sensitive." "Don't hang up." Anything to prevent you from thinking too hard.
- They ask you to act. Transfer money. Share a verification code. Confirm your account details. Wire funds to a "safe" account.
The newer twist: instead of the traditional "Nigerian prince" energy, these calls sound professional. They sound like someone you'd actually talk to. That's the whole point.
Red Flags That Still Work
Even with AI making these scams more convincing, the underlying tactics haven't changed much. Watch for:
- Urgency + secrecy. "Act now, don't tell anyone, this is confidential." Real emergencies rarely require you to hide things from other people.
- Requests to move money. No legitimate bank or company will ever ask you to transfer money to "protect" it. Your money is fine where it is.
- Verification code requests. Banks use these to prove you're you. If someone asks for your code, they're trying to prove they're you. Huge red flag.
- "Don't call back." If they discourage you from hanging up and calling a number you find yourself, that's because you'd reach the real company and blow their cover.
- Emotional manipulation. Fear ("your account is compromised"), obligation ("your boss asked for this"), or love ("your grandson needs bail money"). The CEO impersonation scam is especially nasty because it combines authority with urgency.
The One Rule That Stops Most of This
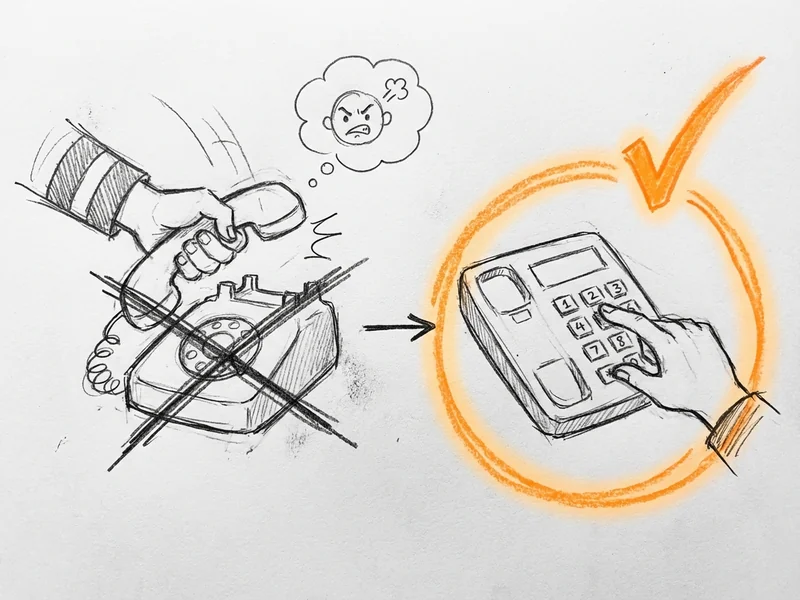
The FTC puts it simply: "Call your real bank, broker, or investment advisor. Use the number you find on your statement—never the number the caller gave you."
That's it. That one habit defeats almost every vishing scam in existence.
Someone calls claiming to be your bank? Say "Thanks, let me call you back" and hang up. Then call the number on your debit card or bank statement—not the number they gave you, not the number in your recent call history. The real number. If there's actually a problem, they'll know about it.
Same goes for your boss, your mom, your accountant. If they're asking for something unusual, hang up and call them directly on a number you already have. Thirty seconds of verification can save thousands of dollars.
What About Voice Recognition?
"But I know what my mom sounds like." Sure. And so does the AI.
Here's a family-level protection that actually works: create a verbal codeword. Something only your inner circle knows. If someone calls in an emergency, they have to say the word before you take any action. No code? No money, no information, no help until you verify through another channel.
It sounds paranoid until you remember that scammers have cloned voices to trick parents into thinking their kids were kidnapped. At that point, a codeword doesn't seem paranoid at all—it seems like common sense.
For Business Owners: Protect Your Team
If you run a small business, your team is a target. The scammer pretending to be you asking your bookkeeper to wire funds is a real and growing threat.
Some practical steps:
- Two-person rule for money movement. Any wire transfer, large payment, or bank change needs approval from two people. Period.
- Verbal verification for anything urgent. If an "urgent" request comes in via voicemail or phone, confirm it through a different channel before acting.
- Train your team. Make it okay to question requests that feel off. Better to have an awkward "Hey, was that really you?" call than to lose $10,000.
- Limit public voice exposure. That podcast interview or conference talk? Great for marketing, but also great for voice cloning. It's a tradeoff worth being aware of.
What to Do If You've Been Hit
If you realize you've fallen for a vishing scam:
- Contact your bank immediately. The faster you act, the better chance of stopping or reversing a transfer.
- Report it. File a complaint with the FBI's Internet Crime Complaint Center and the FTC.
- Document everything. Save call logs, voicemails, any communications. You may need this for fraud investigations or insurance claims.
- Change passwords. If you shared any account information, assume it's compromised and change credentials immediately. (If you don't have a password manager yet, now's the time.)
- Warn others. If scammers have your family's or company's information, they may target other people you know.
And don't beat yourself up. These scams are designed by people who do this full-time. Smart, careful people fall for them regularly.
The Bottom Line
AI didn't create phone scams. But it made them a lot more convincing. The person on the other end of that urgent call might not be a person at all—just software reading a script in a cloned voice.
The good news: the defense hasn't changed. Hang up. Call back on a number you trust. Verify before you act.
When in doubt: always call back.
Questions about keeping your business safe from these scams? Give me a call—this stuff isn't complicated once you know what to look for, and a little preparation goes a long way.

